The word “IP address” has been thrown around very often in the internet space. And if you’re a novice, you may have heard about it several times yet unable to fathom the meaning. Well, you’ve landed on the right page, and we will try to demystify it for you—among other essentials to hiding it from hackers and prevent its restrictions.
What is an IP address?
An IP address is an address through which your computer sends out and receives data. To paint a clearer picture, imagine as a street address. The street contains different houses, each with their respective addresses. The same goes for the computer that connects to the internet—they have their individual “street addresses,” which is the IP address.
Every computer, phone, or a server that is on the internet has an IP address. When you’re about to load a website, your computer will send out a request to that website IP address to release its content. The content will go back to the PC via the computer’s IP address.
A similar scenario plays out when you send a letter to someone. You’ll require their address to get your letter across to them—and will need yours to return a similar letter to you too.
There is a belief that an IP address contains a wealth of information, and people can find your name, location, and other sensitive personal information in the process. But is that in line with the truth?
Probing further, can your IP address hand out your personal information or your web browsing history? This area of internet security throws in so much confusion with all sorts of myths in between. So the question now is: What does an IP address reveal?
Also Read: Difference Between SeedBox vs VPN? Explained Clearly
What an IP address can reveal?
Looking up an IP address tool to verify your location, you’ll discover that the items revealed are IP address, ISP, hostname, and geographical identifiers.
There may be variations in geographical identifiers, but most time your country, continent, state or region, city, and postcode will come up. The actual postcode will not show up, instead, a partial one. Aside from this information, nothing else is revealed.
What an IP address does not reveal?
People have built up wrong perceptions about what an IP address reveals —no name, date of birth, or your address will be shown. Nothing else is put out there except the information stated earlier.
However, if the ISP administrator permits it, more information can be obtained from the IP address. The network administrator can alter the information that is available when displaying IP addresses. In most cases, ISPs will keep the security level high while revealing the least amount of information.
It is the standard practice anywhere in the world and the ethical thing to do when you protect the user’s identity and privacy. In a situation where extra information is needed about a particular IP address, the inquirer will have to contact the Internet Service Provider or administrator and present a direct request. Often, the request is denied except in a police investigation situation.
So there you go! Contrary to perception or belief, our IP addresses are no gateway to our personal information. And with a reliable ISP provider, your IP address will never reveal anything other than basic information about your location.
Potential Risks to what your IP Address Reveals
As you already know, every computer connected to the internet comes with an IP address. If you have to send emails, there must be an IP address—you’ll also have an IP address even to buy online. The process is simple: As soon as you get connected, your IP is active, and your IP can change depending on your location.
But hackers can still target our IP addresses. Hackers are always on the move to disrupt the system, launching their attack at the sight of a loophole. If you’re not well-protected, you could be biting your fingers much later for data loss or something of the sort. Nobody wants that kind of scenario.
A Building with several Rooms in it
Let’s say you connect to the internet and you’re running a program at the same time. A port will open, and a number usually identifies it. The drawback is that someone with your IP addresses—a hacker in this case—could gain access to your connection and infects the program you’re running.
From the Back Door
The “rooms” are self-contained without connecting doors to each other as located on your computer. This is a way to describe the ports on your computer. In case a hacker has access to your IP address and finds his way to your port via the back door, they can’t move past that stage—it is a risk in itself for them to have found their way there.
Is there a way to prevent all of these potential risks from happening? Well, you can mask your activities and block the intruder from getting to you. Masking your IP is the best solution—that way, you’re safe and can go on with your online activities worry-free.
Also Read: Best Cheap Seedbox Service Providers
What does it mean to mask an IP address?
When you mask your IP, you hide it from prying eyes to avoid detection. People mask their IP for different reasons.
But one of the biggest reasons is to avoid being tracked. Another reason is because of geographical restrictions. The government may block some content in specific locations, for example, China and the Middle East. If it is possible to hide behind your IP and make it look like you’re surfing the internet from another region, you’re good to go. You can get quickly past these restrictions and view the website that was blocked.
Masking Your IP with VPN and Proxy
There are two ways to mask your IP address—by using a Virtual Private Network (VPN) or a proxy service.
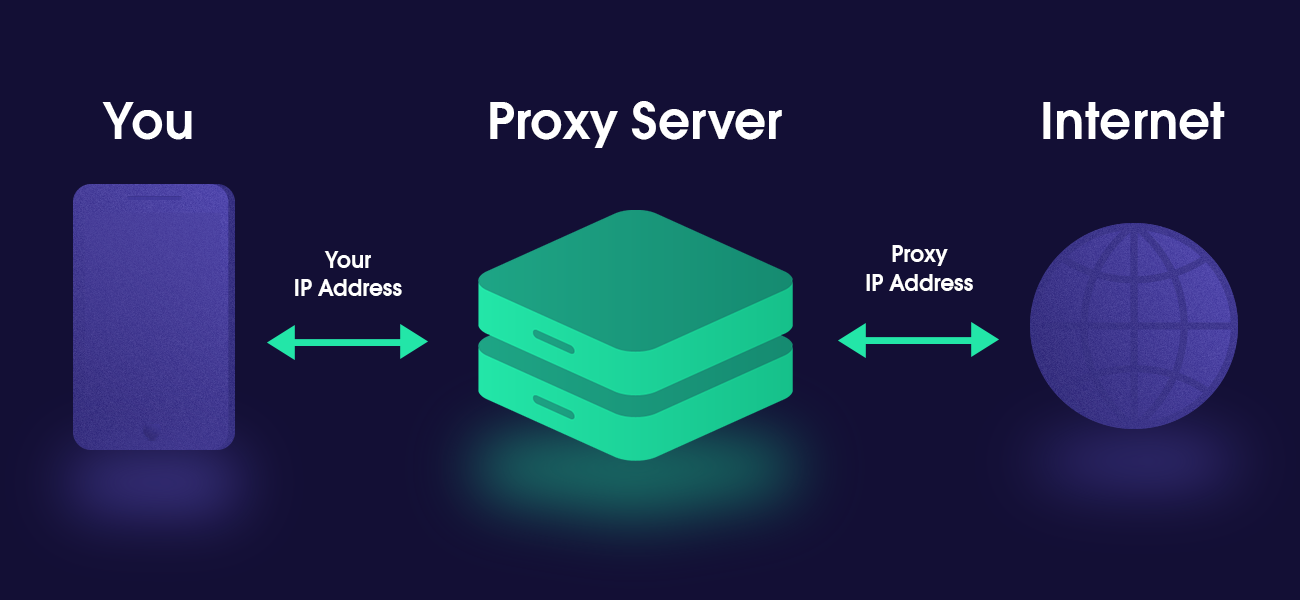
Firstly, a proxy server is an intermediary server that allows your traffic to be routed. The internet servers will only be able to see the IP address of the proxy server—and not that of your IP address. As websites’ servers send information back to you, it is directed to the proxy server after which it is then routed to you.
It’s as simple as that, but if you would like to get to the bottom of proxy fundamentals, check out Oxylabs – premium proxy server provider – take on what is a proxy.
Whereas, a VPN also does something quite similar. When a device is connected to a VPN, the computer acts like it is on the same local network as the VPN. All network traffic goes over a secure connection to the VPN. Your device will behave like it is on the system, and you can access local network resources even when you’re on another side of the world.
Again, you’ll use the internet like you’re present at the VPN’s location. This comes with some benefits if you’re on public Wi-Fi, or you want to gain access to geo-blocked websites.
Browsing the web while you’re connected to a VPN means your computer connects to the website via the encrypted VPN connection. The VPN will forward the request, including the response from the site via a secure connection. For example, if you’re accessing Netflix through a USA-based VPN, Netflix will think the link is from within the USA.
Benefits of using VPNs and Proxies
- VPNs and proxies will allow you to gain access to restricted websites and other areas with a unique IP address. You’ll gain access much faster as they cache sites or pages which will take faster to reload when trying to access them the second time.
- A proxy stands in between you and the site you’re trying to access. This gives a level of security, as well as anonymity where the IP address registered that is outside your network is the server’s IP address.
- A high level of encryption protects VPNs and allows you to browse the web without fear of being exposed.
- VPNs usually offers faster speed than proxy servers—and features better security. Users can choose the server location of their choice; you can use them on both computers and mobile.
- VPN providers now offer subscription features of a one-touch setup. That means it is user-friendly, with newbies having no problem during installation—and can surf the net safely in a matter of minutes.
- A proxy server will protect a user’s information from getting into the wrong hands.
- Some proxy servers offer performance improvement by using compression tools and file caches to load internet content faster.
- For users connected via proxy in that office, they will gain access to any content already accessed by others faster than those not on a VPN.
Also Read: Top 11 Most Sought-After JavaScript Widgets
Drawbacks of VPNs and Proxies
Using VPNs and proxies sure have drawbacks too.
- Information going through a proxy server may be intercepted by a third party—especially in the case of a free proxy because they’re not encrypted.
- VPN subscription comes at a cost every month.
- Users of proxies may be exposed to malware as they come with spammy advertisements.
- Websites implementing strict user behavior protocols may restrict you with the use of proxies or VPNs, causing security problems. For instance, if you’re accessing PayPal with a VPN, your account may be flagged as being suspicious because it would appear your location has changed. That could cause an unnecessary problem, and the user will have to contact support.
- VPN and proxy server engenders prohibited activity. Users will gain access to restricted sites and can download regulated information and files like music, movies because they’re anonymous. For this reason, so many sites are putting in place stricter security measures meant to target VPN users.
- Free VPN apps are everywhere and ideally suited for Apple devices and Android. They can lure you into installing them. But some of them have nothing to offer you because they’re fake VPN services. They could collect and sell your information, putting you in a difficult situation. They barely do what they promise—like protecting your data.
- You may have proper encryption using a VPN, but it usually comes with an element of lag. When you use a VPN service, it can slow down your Internet connection’s speed due to the amount of processing power involved for encryption. For an optimal connection speed, a decent commercial VPN service will have to come into the picture.
Don’t fret! Your IP is not in any way revealing your personal information except your ISP allows it—which most certainly doesn’t happen. You may want to leverage the benefits of VPN and proxies to your advantage going forward. Use them ethically and keep the prying eyes of hackers away from your business.